- info@securotix.com
- 808-The Burlington Tower, Business Bay, Dubai (UAE)
Get In Touch
+971 55 651 2218

LogRhytham
- Home
- LogRhytham
LogRhythm Threat Management Ecosystem Threats Have Evolved—Has Your Security Program?
The perimeter is gone. Data is everywhere. Threats are sophisticated and motivated. It’s never been more important for you to detect and respond to them quickly. They use many direct and indirect attack vectors. The volume of security alarms is overwhelming. Prevent threats, attacks and compromises to your IT infrastructure from damaging your business by proactively managing the attack lifecycle.
Detect and Kill Threats Early
Data breaches don’t happen overnight. Threats must first penetrate your environment and then be allowed to operate undetected—for weeks or even months. To avoid data breaches and other damaging cyber incidents, detect and kill threats early in their lifecycle.
Reconnaissance
The threat actor assesses your defenses, and how to perform the initial compromise. Whether through spear phishing, remote zero-day exploit, physical compromise or stealing credentials, they will find a way in.
Initial Compromise
The threat actor determines their target and gains initial entry to your network. This could be a compromised endpoint device or a compromised account. They can now authenticate within the internal network.
Command & Control
The threat actors put back doors and remote access tools (RATs) in place. They can now stealthily return at any time to continue their mission.
Lateral Movement
The threat actor scans your internal network, identifying additional targets. They compromise more systems and more user accounts. Their foothold and access in your environment is now widespread.
Target Attainment
The threat actor identifies and finally gains access to the systems of interest. They now have all the access they need to realize their objective.
Exfiltration, Corruption and Disruption
The threat actor realizes their mission. They might siphon off data via covert communication channels. Or they might disrupt a critical business operation. In either case, they have done real damage. The costs for your organization to recover could now measure in the millions.
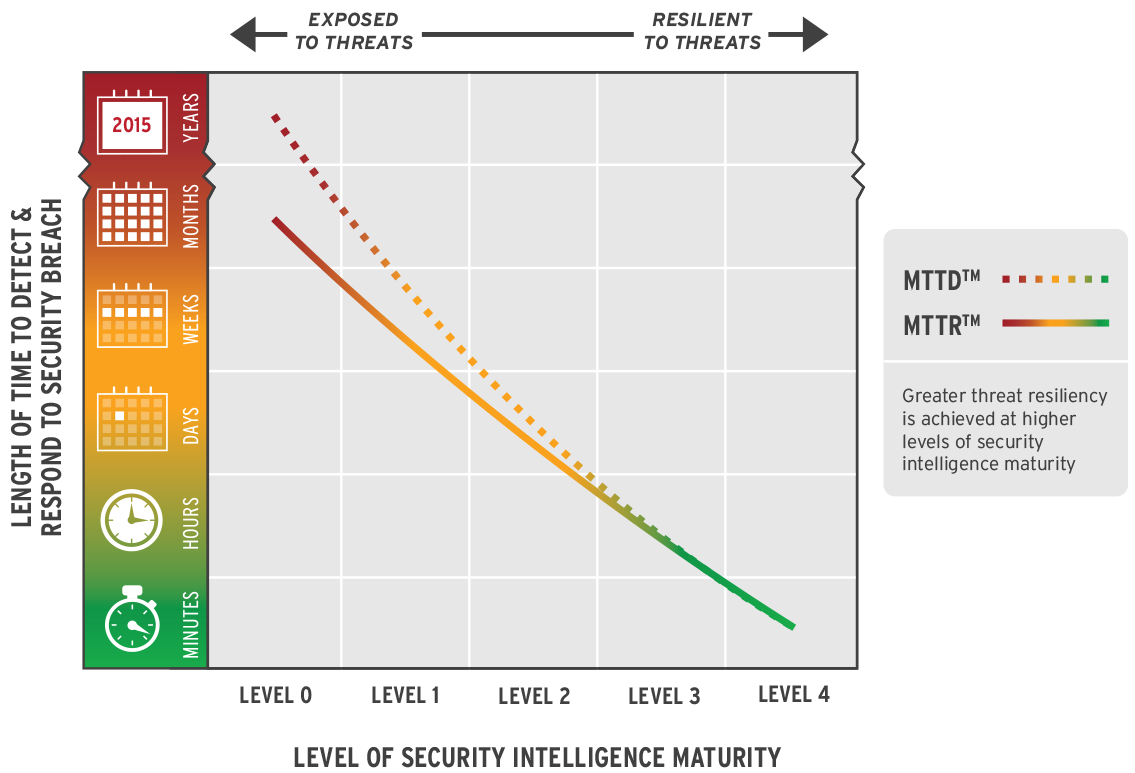
Dramatically Reduce Detection and Response Times
To kill threats quickly, you need to accelerate time to detection and time to response. This requires efficiency of operations and a well-enabled team. The LogRhythm platform optimally serves both needs by delivering end-to-end Threat Lifecycle Management. Efficiently reduce your mean-time-to-detect (MTTD) and mean-time-to-respond (MTTR) with LogRhythm.
Streamline Your Security Operations
The effectiveness of your security monitoring and response program is largely determined by the efficiency of your workflows. How many alarms can your team qualify every day? How many investigations can they conduct? How quickly can they respond to incidents?
Your answers to these questions are either enabled or impeded by workflow efficiency. The LogRhythm Security Intelligence Platform delivers a streamlined workflow, from detection through mitigation to full recovery. You’ll see more, investigate more and respond more quickly.
Collect
You can’t detect what you can’t see. LogRhythm collects machine data from across the enterprise and augments this machine data with critical context. LogRhythm’s network and endpoint forensic sensors provide further visibility across the extended IT environment. Learn more about Log Management.
Discover
Our big data analytics approach ensures no threat goes unnoticed. Machine analytics automatically analyze all collected data, detecting both routine and advanced threats automatically. Our powerful search capabilities enable your team to efficiently hunt for threats. Learn more about Security Analytics.
Qualify
The LogRhythm Security Intelligence Platform automatically qualifies all threats with a 100-point risk-based priority score so your team knows where to spend their time. Alarms can be quickly qualified with immediate access to rich forensic detail displayed in user-friendly analysis tools.
Investigate
Ensure that threats don’t slip through the cracks. Enable collaborative investigations by using our embedded incident response capabilities. Obtain real-time visibility into active investigations and incidents with dashboards and live activity feeds.
Mitigate
Our SmartResponse™ automation framework helps you configure pre-staged actions to automate common investigatory steps and mitigations. Enable your analysts and incident response team to investigate and kill threats more quickly.
Recover
Collateral damage often exists after an incident. If you detect the threat late in the lifecycle, you run the risk of additional systems and accounts being compromised. LogRhythm’s incident response orchestration provides central access to all required information. Collaborative workflows bring teams together for rapid recovery.
Workflows that Work
Don’t piece together your workflows–implement a unified workflow for end-to-end threat detection and response. Enable early eradication and avoid the breach.
Use LogRhythm’s built-in incident response orchestration platform to streamline your security operation, accelerate your threat response and reduce risk for your organization. You’ll be able to detect more threats and respond to more incidents.


