- info@securotix.com
- 808-The Burlington Tower, Business Bay, Dubai (UAE)
Get In Touch
+971 55 651 2218

F5
- Home
- F5
How do we know?
We know because companies keep getting their data stolen.Just look at news headlines on any given day.Data breaches keep happening, despite organizations:

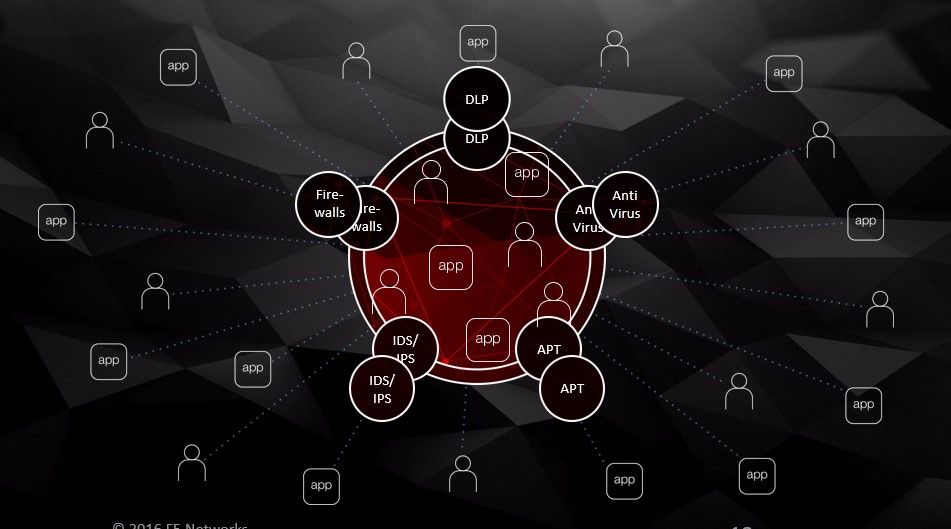
We are still approaching security with a decades-old mindset
that focuses on location-based protection—building walls and barriers.(Note: the red circle represents a traditional perimeter-based approach to security.)
This has led many companies to invest heavily in network-based and specialized security solutions, for example, next generation firewalls, data loss prevention (DLP), Advanced Persistent Threat (APT) solutions, Intrusion detection and intrusion protection (IDS/IPS) systems; anti-virus solutions.
It’s not that these solutions aren’t useful or necessary; they are—each one has its purpose. But, by themselves, they just aren’t adequate anymore.Many are blind to today’s threats,and they’re into what’s happening with your application. That’s because they were never designed to do that.
And consider this: How many employees are directly connected to your corporate network anymore?Very few. Virtually every worker is mobile at some point during the workday, and your fully-remote users are never directly connected.
With the prevalence of cloud-based and SaaS apps, many workers can complete an entire day’s work without ever connecting to the corporate network.
These users, who are mostly outside of your network now, pose an even greater risk to your company because they’re sharing company data using devices, networks, and applications that are beyond your control.What’s the result? (Where does that leave us today?)
NETWORK THREATS
Today, the real data security threat is not happening at the network layer. Yes in the last few years there has been a lot of attacks at the network layer, a lot of money being spent there to prevent viruses, spam, spy-ware; lots of attention being spent here. Attacks at the network layer are highly visible, they affect productivity, they are messy & annoying
APPLICATION THREATS
Who: Threat Actor Groups, Nation-states, Countries & Toolkits. Trends by Geolocation, ASN & Regional Registries
What they are doing: Exploit trends by Target (Identity, App, DDoS), Impacted software
When they are doing it: Timing trends, Continual, Seasonal, Time of Day, Day of Week
How they are doing it: Attack Types, 0-day exploits, Unpatched vulnerabilities, Social engineering, Trends by Targets (geo and industry)
Why they are doing it: Understanding targets and purposes (Financial, Competitive Advantage, Espionage, Notoriety, Cyber warfare)
Then we take it a step further by informing you “what’s next” in emerging attack trends, and how to mitigate a particular threat.
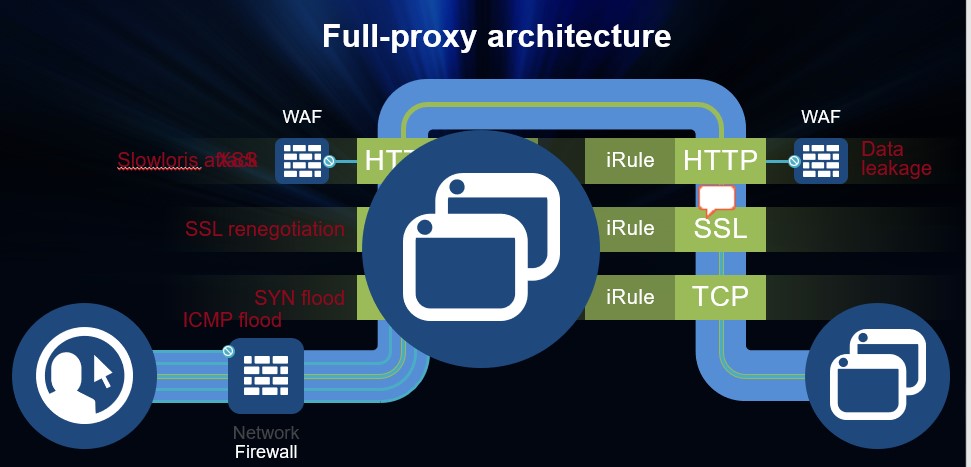
Full-proxy architecture
Speaker notes: Now we’ll show you how we deliver this protection. F5 provides security on a full proxy architecture. We inspect every packet in the flow of traffic and are able to profile that at every layer of the OSI stack. TCP, SSL, HTTP…we understand everything about these protocols and can take action on threats. And because it’s a full proxy addressing one flow through the stack, all of the processes communicate with each other to gain a full understanding of the attack and apply the most appropriate response.
Additionally, all of these security services are on hardware that is purpose-built to deliver at extremely high performance and scale so you don’t get the performance degradation of typical security solutions. It’s all one box: management and power efficiencies, lower TCO.